Let's see if you can stomach Art the Clown's notorious 'hack saw scene' on the big screen! Be sure to bring your barf bags.” - Director… | Instagram

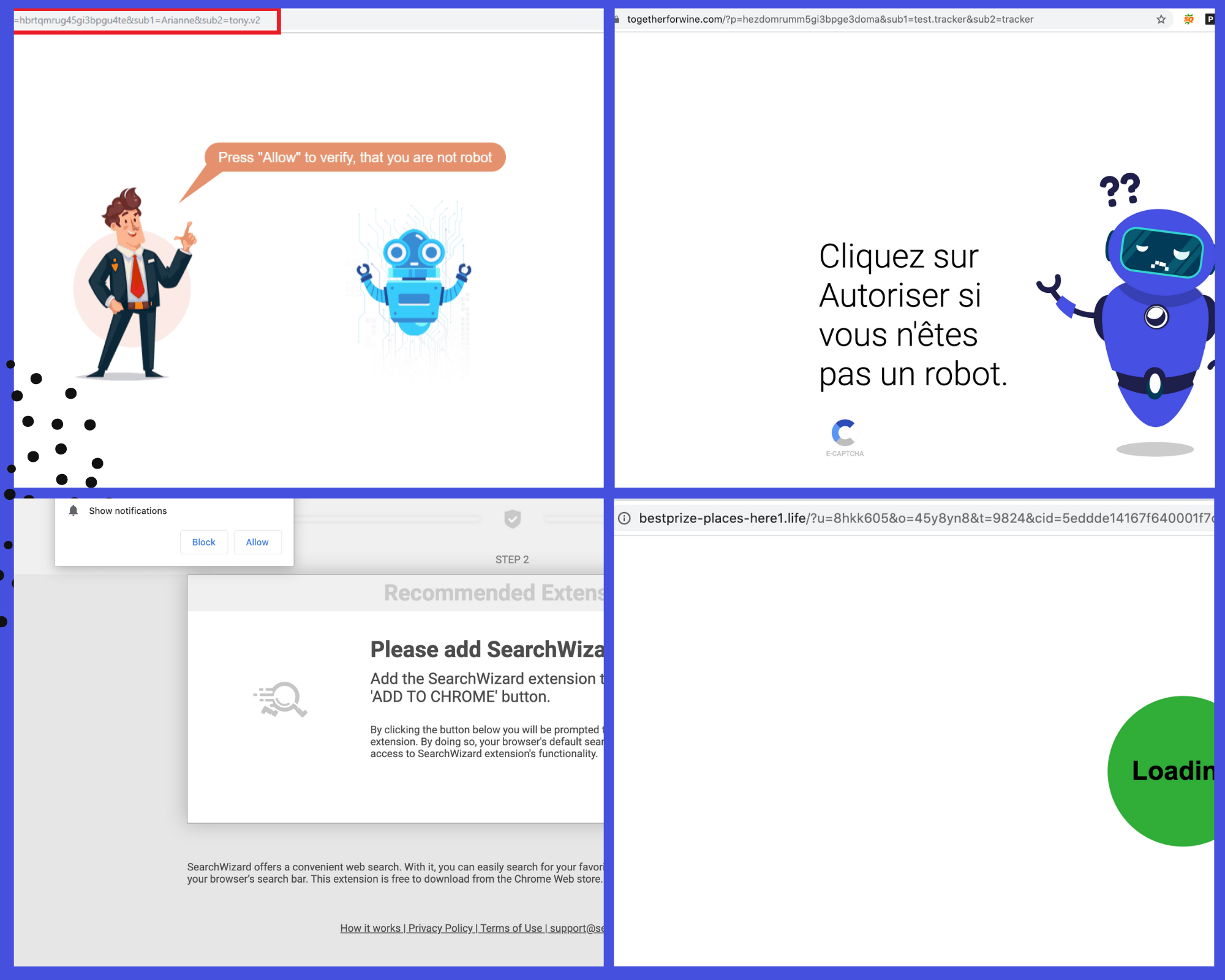
Attacking A Virtual Toaster: An Experiment Shows How Quickly The Internet Of Things Can Be Hacked : All Tech Considered : NPR

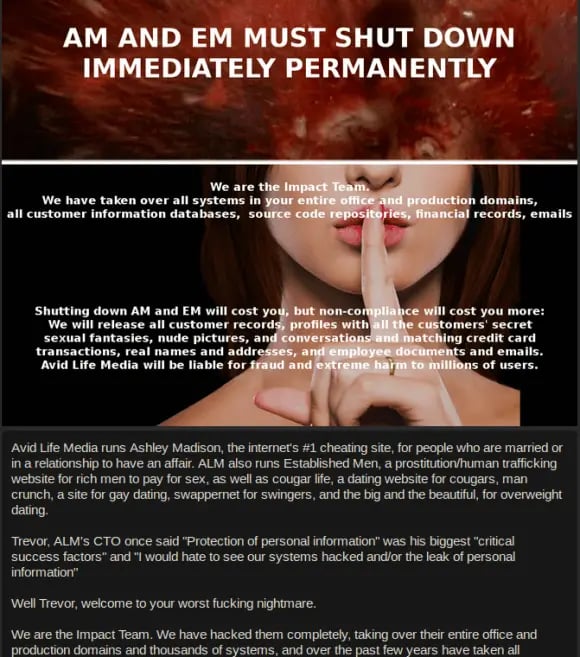
How the Colonial Pipeline hack is part of a growing ransomware trend in the US | Cybercrime | The Guardian

Service Dog Training Guide: A Step-by-Step Training Program for You and Your Dog - Kindle edition by Hack, Jennifer. Crafts, Hobbies & Home Kindle eBooks @ Amazon.com.


/cloudfront-us-east-1.images.arcpublishing.com/gray/SAFRLLO3UBDHXG7SZESDTNYO2E.png)